O365 / Microsoft / Azure SSO Setup: Difference between revisions
(Created page with " This page is part of the NOVA Teams guides. =Azure Active Directory / Microsoft Entra ID= ===Registration=== Once the email is received, copy the code provided to you at the bottom, and then click the ['''Complete]''' button<blockquote>frameless|1033x1033px You will then be redirected to a web page to sign in with your Microsoft Admin credentials Accept/Consent to all of the messages, this is you granting our connector acce...") |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
This page is part of the [[NOVA SSO|NOVA | This page is part of the [[NOVA SSO|NOVA SSO]] guides. | ||
This page should only be used if you are a reseller partner and have your own landing portal.<blockquote>'''Vested Networks customers do not need to perform the steps below, SSO can be enabled by any of our support technicians if you call in.'''</blockquote> | |||
=Azure Login= | |||
Login to https://portal.azure.com with your developer account | |||
=== Azure Active Directory / Microsoft Entra ID === | |||
Select Azure Active Directory service (now known as Microsoft Entra ID). If it is not visible on the dashboard, you can use the search function to find it. | |||
Select App registrations from the side pane. | |||
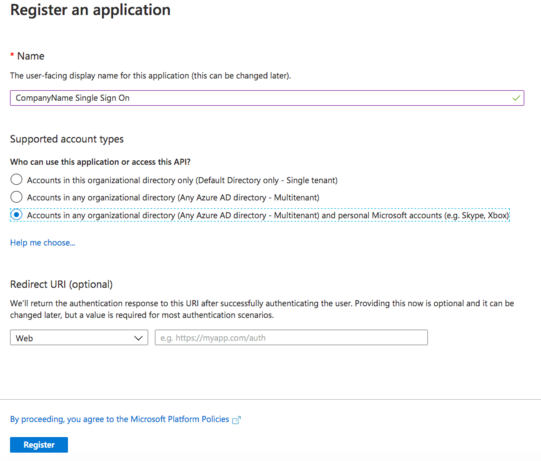
Register a New Application (if not previously performed) by clicking the "+new registration" button/link in the center pane. | |||
=== | |||
==== Register an application ==== | |||
The window should look similar to the below:<blockquote>[[File:SSO MS 1.png|frameless|541x541px]]</blockquote> | |||
Select the previously created App registration by clicking the Display name. | |||
Copy the newly created 'Application (client) ID' from the data set in the center of the pane and retain for a future step. | |||
Select Authentication from the side pane. | |||
==== Configure Platform ==== | |||
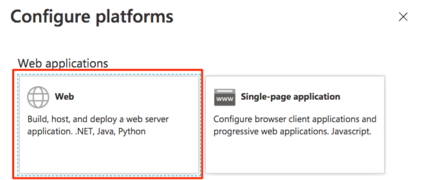
Under Platform Configurations choose "+Add a platform." | |||
In the resulting Configure platform pane, select Web<blockquote>[[File:SSO MS 2.png|frameless|424x424px]]</blockquote> | |||
===== Configure Web ===== | |||
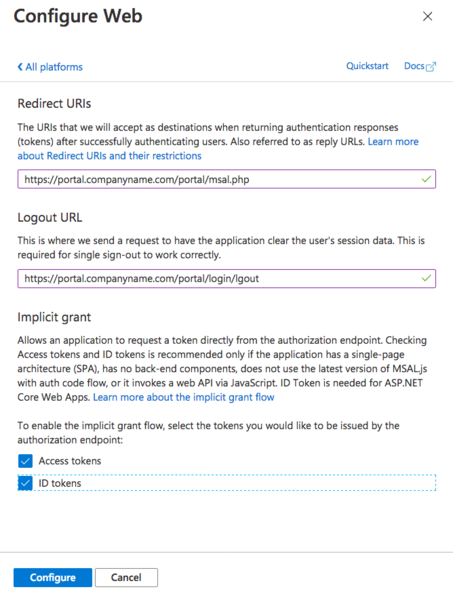
In the resulting Configure Web pane, enter one of the required Redirect URLs, the Logout URL and select Implicit Grant for both Access tokens and ID tokens. When complete click Configure. | |||
Redirect URI: | |||
* <nowiki>https://nova.vestednetworks.com/portal/msal.php</nowiki> | |||
Logout URL: | |||
* <nowiki>https://nova.vestednetworks.com/portal/login/logout</nowiki> | |||
The window should look similar to the below (but I bet you spelled logout correctly):<blockquote>[[File:SSO MS 3.png|frameless|600x600px]]</blockquote> | |||
===== Add Redirects ===== | |||
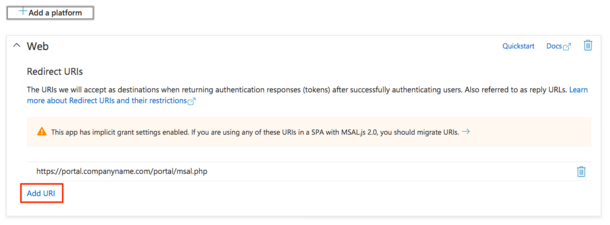
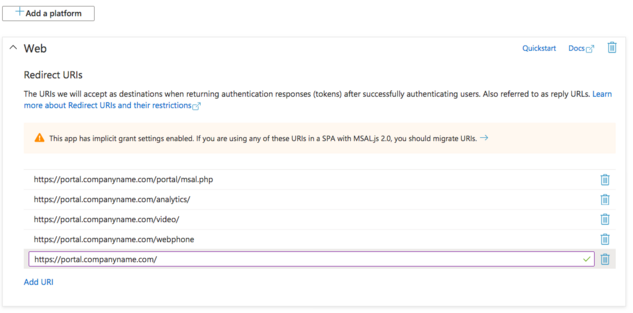
Add the remaining required Redirect URLs by using the Add URI link at the bottom of the Web platform box.<blockquote>[[File:SSO MS 4.png|frameless|610x610px]]</blockquote>ALL required Redirect URIs are below: | |||
* <nowiki>https://{subdomain}.{FQDN}.com/portal/msal.php</nowiki> (Added above) | |||
* <nowiki>https://{subdomain}.{FQDN}.com/analytics/</nowiki> | |||
* <nowiki>https://{subdomain}.{FQDN}.com/video/</nowiki> | |||
* <nowiki>https://{subdomain}.{FQDN}.com/webphone</nowiki> {no trailing slash) | |||
* <nowiki>https://{subdomain}.{FQDN}.com/</nowiki> ''({subdomain}.{FQDN} like nova.vestednetworks.com)'' | |||
===== Review and Save ===== | |||
The Web platform box should look similar to below:<blockquote>[[File:SSO MS 5.png|frameless|633x633px]]</blockquote>Click "Save" at the top of the page. Your Office 365 SSO service will now be fully configured and enabled on Azure.<blockquote>[[File:SSO MS 6.png|frameless|716x716px]]</blockquote> | |||
'''NOTE''': You should have "personal Microsoft accounts" listed in the "Supported account types" section. If missing, navigate to the Manifest and set the 'signInAudience' parameter to "AzureADandPersonalMicrosoftAccount" | |||
Once this has been enabled, Vested Networks will need to know the 'Application (client) ID' that was retained from above so that we can put it in our system and then we can enable the SSO on our end. | |||
'''If you have any questions about this process, or if you need assistance, please reach out to our Support Team by dialing HELP (4357) on your desk phone, calling (972) 924-6488, or emailing help@vestednetworks.com.''' | |||
Latest revision as of 15:15, 16 October 2025
This page is part of the NOVA SSO guides.
This page should only be used if you are a reseller partner and have your own landing portal.
Vested Networks customers do not need to perform the steps below, SSO can be enabled by any of our support technicians if you call in.
Azure Login
Login to https://portal.azure.com with your developer account
Azure Active Directory / Microsoft Entra ID
Select Azure Active Directory service (now known as Microsoft Entra ID). If it is not visible on the dashboard, you can use the search function to find it.
Select App registrations from the side pane.
Register a New Application (if not previously performed) by clicking the "+new registration" button/link in the center pane.
Register an application
The window should look similar to the below:
Select the previously created App registration by clicking the Display name.
Copy the newly created 'Application (client) ID' from the data set in the center of the pane and retain for a future step.
Select Authentication from the side pane.
Configure Platform
Under Platform Configurations choose "+Add a platform."
In the resulting Configure platform pane, select Web
Configure Web
In the resulting Configure Web pane, enter one of the required Redirect URLs, the Logout URL and select Implicit Grant for both Access tokens and ID tokens. When complete click Configure.
Redirect URI:
- https://nova.vestednetworks.com/portal/msal.php
Logout URL:
- https://nova.vestednetworks.com/portal/login/logout
The window should look similar to the below (but I bet you spelled logout correctly):
Add Redirects
Add the remaining required Redirect URLs by using the Add URI link at the bottom of the Web platform box.
ALL required Redirect URIs are below:
- https://{subdomain}.{FQDN}.com/portal/msal.php (Added above)
- https://{subdomain}.{FQDN}.com/analytics/
- https://{subdomain}.{FQDN}.com/video/
- https://{subdomain}.{FQDN}.com/webphone {no trailing slash)
- https://{subdomain}.{FQDN}.com/ ({subdomain}.{FQDN} like nova.vestednetworks.com)
Review and Save
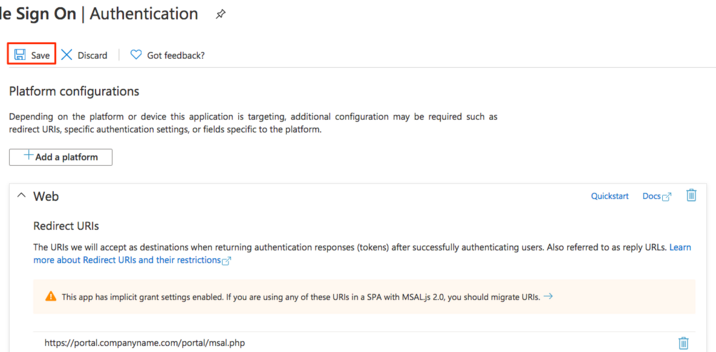
The Web platform box should look similar to below:
Click "Save" at the top of the page. Your Office 365 SSO service will now be fully configured and enabled on Azure.
NOTE: You should have "personal Microsoft accounts" listed in the "Supported account types" section. If missing, navigate to the Manifest and set the 'signInAudience' parameter to "AzureADandPersonalMicrosoftAccount"
Once this has been enabled, Vested Networks will need to know the 'Application (client) ID' that was retained from above so that we can put it in our system and then we can enable the SSO on our end.
If you have any questions about this process, or if you need assistance, please reach out to our Support Team by dialing HELP (4357) on your desk phone, calling (972) 924-6488, or emailing help@vestednetworks.com.